Matlab:数模01-层次分析法
本文共 1260 字,大约阅读时间需要 4 分钟。
本文目录:
====================================================
一致矩阵法



上方该表,按照图二的参考体系,C1与自己比较为1。c1和c2比较为1/2,这意味着c1为1,c2为2,即c2比c1更重要一些。以此类推。
层次性检验(例子)
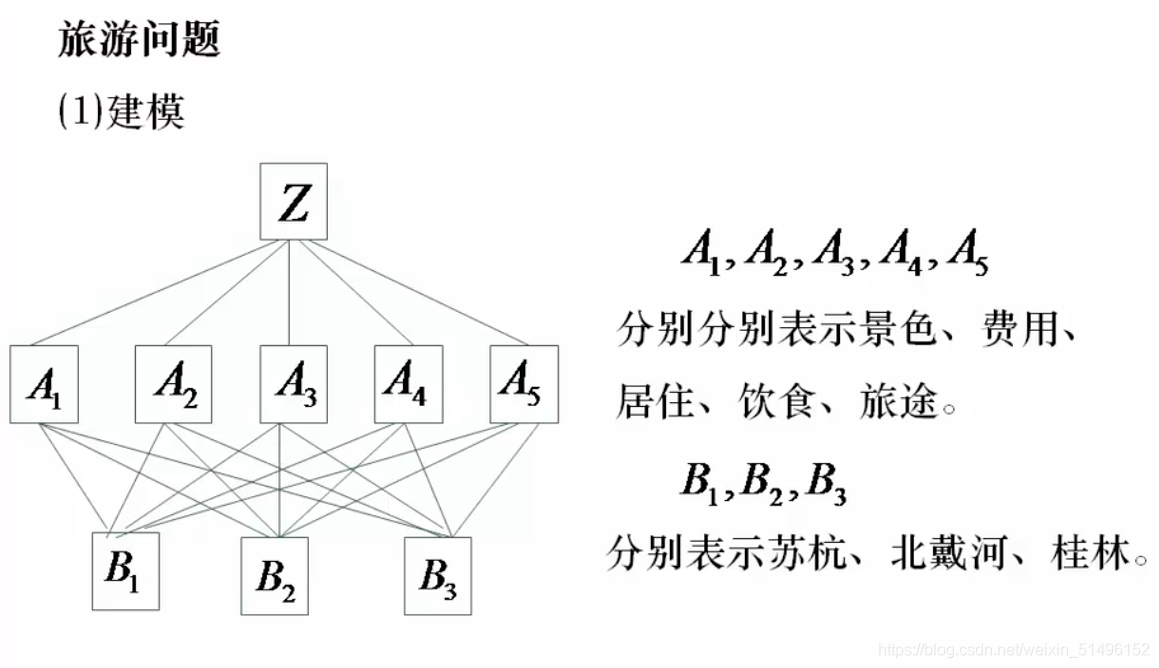
 上面的矩阵A是我们前文提到过的数据。下方的矩阵B1~5的数据都是自己创造的,不是计算得来的,这点要注意。同时线图B1~3和矩阵B1~5没有任何名字上的关系。
上面的矩阵A是我们前文提到过的数据。下方的矩阵B1~5的数据都是自己创造的,不是计算得来的,这点要注意。同时线图B1~3和矩阵B1~5没有任何名字上的关系。 如矩阵B1,就是

b1:b2也就是苏杭和北戴河相比的意思,与上文的比较体系是同样的。
接下来给出一个具体数据,我们使用Matlab解决。
Matlab代码
disp('请输入判断矩阵A(n阶)');A=input('A=');[n,n]=size(A);x=ones(n,100);y=ones(n,100);m=zeros(1,100);m(1)=max(x(:,1));y(:,1)=x(:,1);x(:,2)=A*y(:,1);m(2)=max(x(:,2));y(:,2)=x(:,2)/m(2);p=0.0001;i=2;k=abs(m(2)-m(1));while k>p i=i+1; x(:,i)=A*y(:,i-1); m(i)=max(x(:,i)); y(:,i)=x(:,i)/m(i); k=abs(m(i)-m(i-1));enda=sum(y(:,i));w=y(:,i)/a;t=m(i);disp(w); %以下是一致性检验CI=(t-n)/(n-1);RI=[0 0 0.52 0.89 1.12 1.26 1.36 1.41 1.46 1.49 1.52 1.54 1.56 1.58 1.59];CR=CI/RI(n);if CR<0.10 disp('此矩阵的一致性可以接受!'); disp('CI=');disp(CI); disp('CR=');disp(CR);end 测试

将以下矩阵输入进去试试:
[1, 1/2, 4, 3, 3;
2, 1, 7, 5, 5; 1/4, 1/7, 1, 1/2, 1/3; 1/3, 1/5, 2, 1, 1; 1/3, 1/5, 3, 1, 1;]

其中CI是一致性指标 ; CR是 一致性比率; RI 是随机一致性指标 。CR<0.10才能通过一致性检验。
结果分析
数据所得的
 即为打分时的权重。
即为打分时的权重。 比如这五个数字中最高的,为0.4758,对应的是费用。也就是说,在决策的五个变量中,费用是最能影响我们决策的变量。
而最低数字的0.0538对应的是居住,也就是说,出门游行,居住是相对而言最不重要的因素。
我们将所有数据都输入进去并将结果展示如下图:


{0.3,0.245,0.455}的意思可以理解为,根据个人喜好得出的最优决策比例B1(苏杭):B2(北戴河):B3(桂林)为0.3:0.245:0.455。所以最优的选择就是桂林。
转载地址:http://pyse.baihongyu.com/
你可能感兴趣的文章